在渗透测试中使用fuzz技术
背景
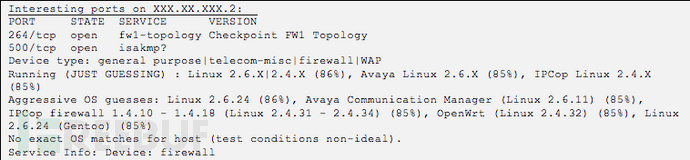
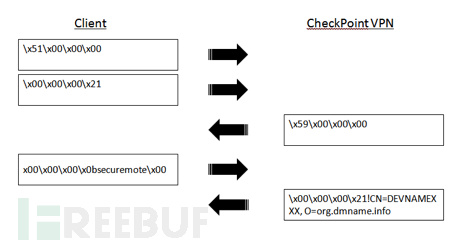
协议分析
工具选择
#!/usr/bin/env python # Fuzzing the initial 4-byte packet from client to CheckPoint VPN server. import time import sys from sulley import * # Time to wait between mutations SLEEP_TIME=0.5 # Time to wait before claiming a host is unresponsive TIMEOUT=3 # number of crashes to observe before skipping the remainder of a group CRASH_THRESHOLD=3 # Initialize the Sulley mutation descriptor s_initialize("SecuRemote-Initial-Packet") s_byte("\x51",full_range=True) s_static("\x00\x00\x00") print "Total mutations: " + str(s_num_mutations()) + "\n" print "Minimum time for execution: " + str(round(((s_num_mutations() * (SLEEP_TIME))/3600),2)) + " hours." print "Press CTRL/C to cancel in ", for i in range(5): print str(5 - i) + " ", sys.stdout.flush() time.sleep(1) # For debugging purposes, uncomment these lines to see Sulley's mutations # in hex dump format #print "Hex dump mutation output:" #while s_mutate(): # print s_hex_dump(s_render()) sess = sessions.session(session_filename="SecuRemote-Initial-Packet.sess", sleep_time=SLEEP_TIME, timeout=TIMEOUT, crash_threshold=CRASH_THRESHOLD) # Tie this session to the SecuRemote-Simple-String fuzzing cases sess.connect(s_get("SecuRemote-Initial-Packet")) # Change this IP address to the target system target = sessions.target("127.0.0.1", 264) # Add the target to the session (can be repeated for multiple targets) sess.add_target(target) # Kick off the fuzzer, monitoring with WebUI on localhost:26000 sess.fuzz()对有状态的协议进行测试
#!/usr/bin/env python from sulley import * SLEEP_TIME=0.5TIMEOUT=3CRASH_THRESHOLD=3# The function Sulley will run prior to sending each mutation. We leverage # it to setup the target system with the initial packets and response in the # protocol exchange prior to our target packet. def preconn(sock): sock.send("\x51\x00\x00\x00") time.sleep(0.5) sock.send("\x00\x00\x00\x21") # Set a socket timeout on the recv so we aren't waiting indefinitely if # the server crashed from a previous test case. sock.settimeout(5) response = sock.recv(4) print "Setup response: ", for i in response: print "%02x" % ord(i), print s_initialize("SecuRemote-Simple-String") # Create a size field, which is based on the content of the named block # Sulley uses ">" to indicate big-endian values, "<" is little-endian s_size("client-name-string", length=4, endian=">") # This is the block of data used for filling in the s_sizeif s_block_start("client-name-string"): # "securemote" is the default string s_string("securemote") # constant null terminator s_byte("\x00") s_block_end() sess = sessions.session(session_filename="Securemote-Simple-string.sess", sleep_time=SLEEP_TIME, timeout=TIMEOUT, crash_threshold=CRASH_THRESHOLD) # Call preconn() before each mutation is sent to setup the target sess.pre_send = preconn sess.connect(s_get("SecuRemote-Simple-String")) target = sessions.target("127.0.0.1", 264) sess.add_target(target) sess.fuzz()成果
相关文章
HiddenEye免费下载
HiddenEye是一款具备高級作用的当代互联网钓鱼工具,而且还适用Android系统软件。 HiddenEye必须大家的电脑上自然环境考虑下列规定: Python 3 Python...
电脑肉鸡的商业价值_怎样看待电脑肉鸡的价值
电脑肉鸡的商业价值,我们应该怎样看待电脑肉鸡的价值,一起来看看下面的内容吧。 1.盗窃“肉鸡”电脑的虚拟财产 虚拟财产有:网络游戏ID帐号装备、QQ号里的Q币、联众的虚拟荣誉值等等。虚...
Hping的典型性主要用途是啥?
什么叫Hping? Hping是网站渗透测试工作人员和IT安全性质量监督员应用的火爆的数据文件解决专用工具。Hping实质上是一个朝向cmd的TCP / IP数据文件汇编器和解析器。该专用工具适用各...
OSSIM是完全免费的吗?
什么叫OSSIM? OSSIM出示安全性专业人员从SIEM商品中出示的全部作用 - 恶性事件搜集,归一化和关联性。OSSIM是由注安师建立和发布的,不但必须掌握,并且掌握到很多安全性专业人员遭遇的实...
3389爆破服务器技术全过程与原理
其实爆破服务器很简单的,也是必学的。 3389是一个远程桌面的端口,很多人为了更方便管理服务器,更新服务器上的资源等,经常会开启3389端口,用nastat-an命令可以查看该端口的开启。对...
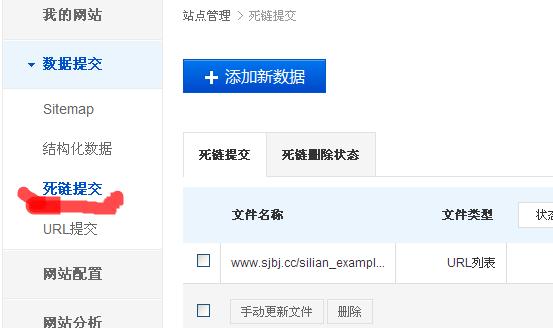
巧妙利用百度站长平台死链工具删除被百度收录的挂马网址
前一段时间,由于程序漏洞造成网页内容多处被挂博彩的内容信息,木马删除后,但是百度收录的挂马页面却都过去几个月了依然还是存在于是利用百度站长平台工具的死链提交将挂马页面删除。下面就为大家分享一下详细的操...

 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!