没有密码怎么找黑客查看我老婆跟别人的微信聊
The following proof of concept demonstrates a XSS virus. The vulnerable environment created is an example scenario required for XSS viruses and does not show an exhaustive set of possible conditions. It illustrates permanent XSS within a web application. In this case, the vulnerability is exploitable via a get request, which allows a trivial virus to be created. Initially an instance of the vulnerable web application will be seeded with the self-propagating code. When this code is executed by web browsers, it results in their infection. The infected web browsers connect to random sites and perform the exploiting get request. The injected code will, in turn, infect further vulnerable web applications with the self-propagating code. The following crafted permanent XSS exploitable PHP page can be infected with a virus. The page accepts a parameter (param) value and writes it to a file (file.txt). This file is then returned in the request to the browser. The file will contain the previous value of the “param” parameter. If no parameter is passed it will display the file without updating it. Web Application: index.php $p=$HTTP_GET_VARS['param'];$filename = "./file.txt"; if ($p != "") {$handle=fopen($filename, "wb");fputs($handle, $p);fclose($handle);} $handle = fopen($filename, "r");$contents = fread($handle, filesize($filename));fclose($handle); print $contents;?> This page (index.php) was hosted on multiple virtual servers within a 10.0.0.0/24 subnet. One web application instance was then seeded with the following code which retrieves a javascript file and executes it. Alternatively, it is possible to inject the entire code into the vulnerable applications rather than requesting a javascript file. For simplicity, a javascript file (xssv.jsp) was requested. Injected Seed Code: The javascript file that was requested in the example is shown below. Its self-propagation uses an iframe which is periodically reloaded using the loadIframe() function. The target site IP address of the iframe is selected randomly within the 10.0.0.0/24 subnet via the function get_
相关文章
手裂口子怎么办(怎样预防手裂口子)
风潇潇!刮风又降温秋天带着“诚意”来了。气温也逐渐寒冷起来,突然转变到空气干燥的季节,咱们的肌肤也随之干燥起来,尤其是双手。干燥粗糙甚至裂口,那么我们如何在寒冷的冬季保护好自己的双手呢?又或者是更严重...
偷偷查他人历史开房记录
宝宝吃饭的时候喜欢打打闹闹怎么办,孩子吃饭不安稳是什么原因呢,孩子吃饭太不听话了不少家长都会抱怨,那么孩子吃饭不安分怎么办呢,友谊长存小编就来说说吧。 所以在面对宝宝“玩饭”或者边玩边吃的行为时,妈...
复方板蓝根对新冠病毒有效-复方板蓝根可体外抑制新冠病毒
新冠肺炎疫情在中国早已处在彻底可控性情况,现阶段中国的诊断病案总数也十分的少,全国各地关心的关键关键在防止新冠上边,除开新冠预苗之外能防止新冠的药品也遭受大伙儿的关心,前不久钟南山表明根据研究发现复方...
免费黑客桌面咋下载(黑客壁纸下载)
本文导读目录: 1、黑客软件如何下载 2、黑客用来扫端口的远程桌面怎么来的,叫什么 3、黑客远程桌面(保护隐私) 4、哪里有的下载电脑黑客帝国数字雨动态壁纸,求网址 5、谁给我点黑客的...
韩国旅游攻略,怎么安排自己的旅行计划
韩国是妹纸们最喜欢去的旅游圣地之一,当你计划去韩国旅游一趟的时候,你想怎么玩,怎么安排自己的旅行计划呢? 你最喜欢哪种出游方式?自由行,跟团游,还是半自由行呢?不管你喜欢哪种,每种方式都有它的...
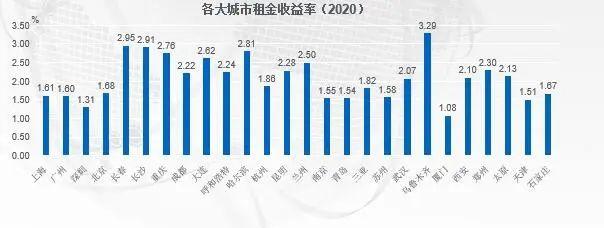
后疫情时代,房价将往哪里走?
主要从六个方面进行分析: 1、缓解疫情冲击全球央行争相放水 2、货币洪水推升资产价格 3、中国房地产价格泡沫高企 4、驱动房价趋势性上涨的人口因素已经发生逆转 5、收入增幅下降和负债比率上升...




 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!